Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
Loading...
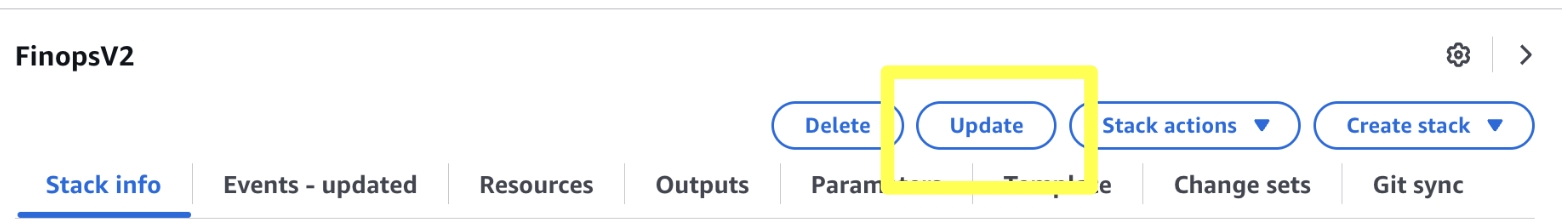
Within your CloudFront Distribution, add customer error response of 403 to / index.html withwith HTTP Response of 200 OK
When preparing for your FinOps Center installation, it's important to consider the design elements related to both your Cloud Estate and the AWS account for your FinOps Center installation.
Aligned with the Multi-Account Strategy, FinOps Center is designed to facilitate the management of your AWS Cloud Estate through the Delegated Admin Account. A Delegated Admin Account may already be created and configured in your Cloud Estate as you set up various AWS Management and Security services like Security Hub and IAM Identity Center.
FinOps Center runs on 100% native AWS Services and is deployed via CloudFormation. FinOps Center is access management services to assist with integrated with core AWS Plaftorm services to simplify AWS Cloud Financial Management.
FinOps Center utilizes the Cost and Usage Data Export report created in the Management Account and replicated to the Delegated Admin. It was designed to work alongside the Cloud Intelligence Dashboard framework, which must be installed prior to the FinOps Center installation.
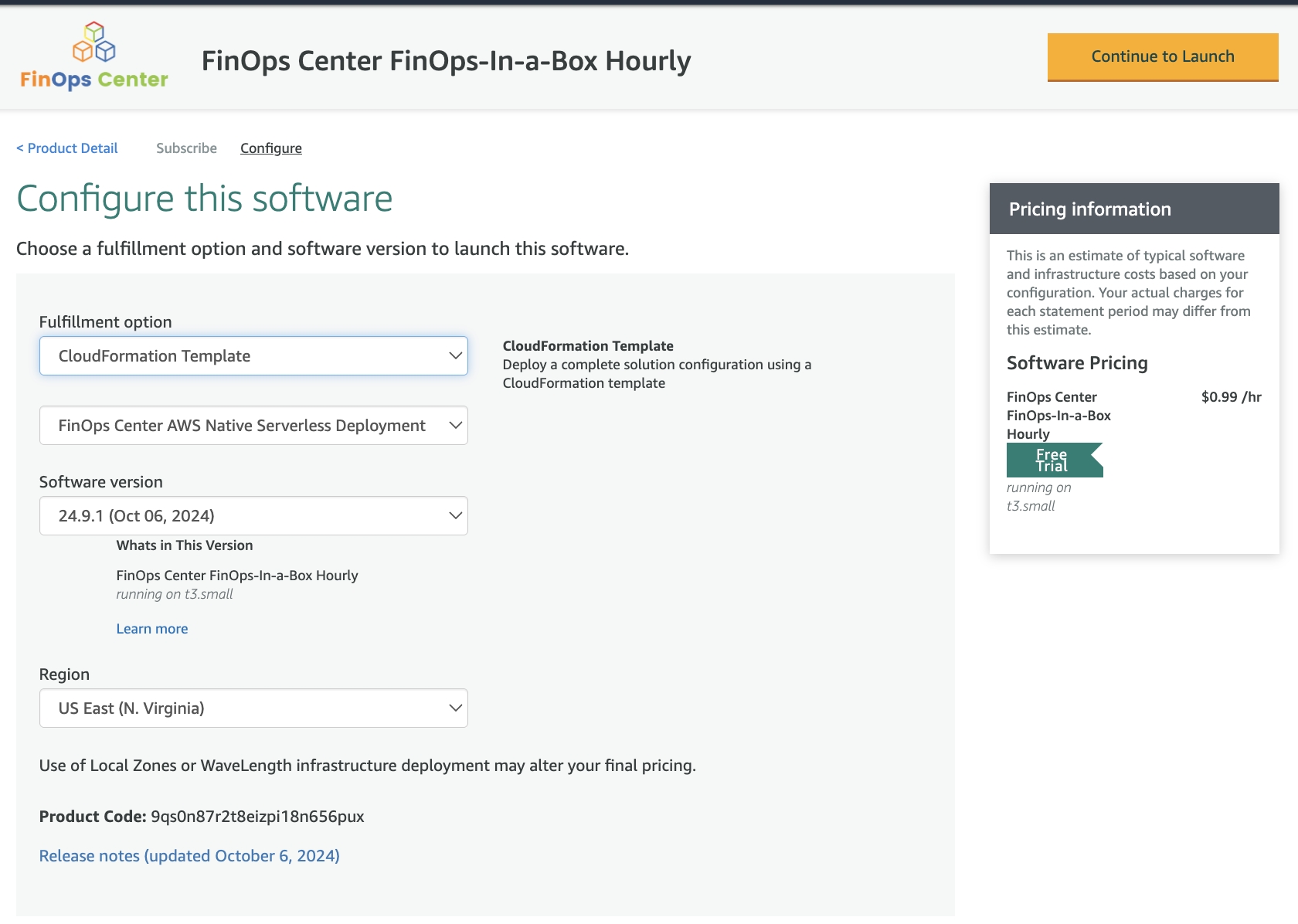
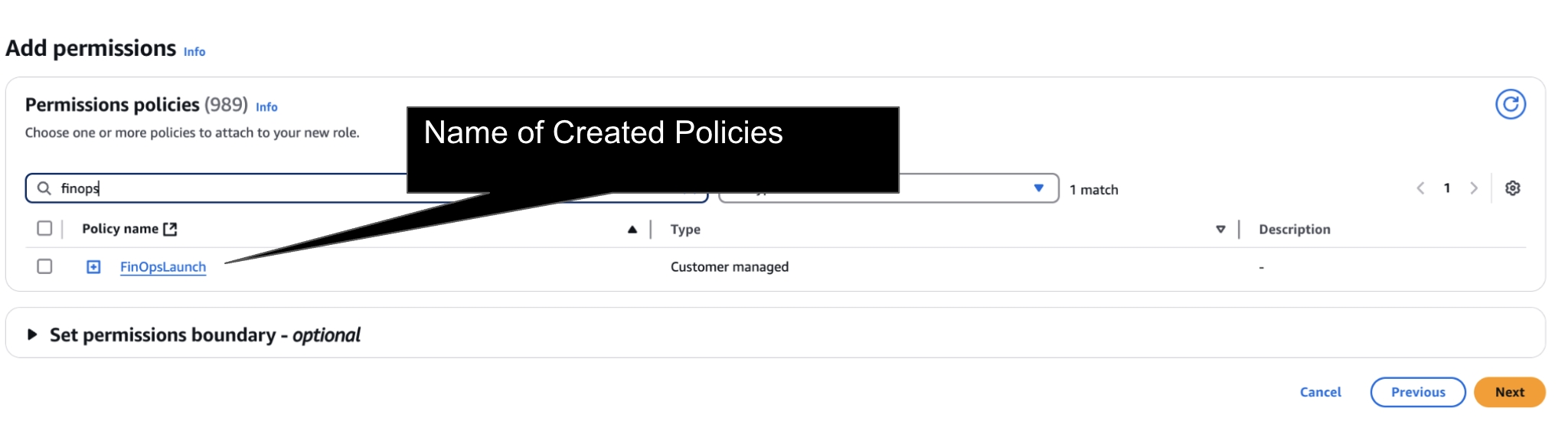
To subscribe to the FinOps Center, the subscription must be initiated and installed from the Designated Admin Account through the AWS Marketplace.
Once the CloudFront Distribution is created, the distribution needs to be configured in your DNS.
If in your DNS is in Route53, add the subdomain the distribution
If in alternative DNS Server, add the distrbution as a CNAME
We build and market our own products while also assisting Customers and ISVs in developing their Agentic Products.
To help Simply to Save with customer's AWS Cloud Financial Management, Cloud Scal3 is please to offer FinOps Center.
To Further Simply and Save with the power of Amazon Bedrock Agentic AI and Amazon Q, Cloud Scal3 is pleased to offer Agent Bill as a complement to customer FinOps Center implementation.
FinOps Center leverages the work from AWS CID Framework that so customer can leverage the Various QuickSight Dashboards created by the OPTICS Team. Scripts need to be run in both the Management and Data Collection Account.
UPDATED Location
To enable the Cost Recommendation Process and Data, the Cost Optimizaton Recommendations need to be enables in both the Master Payer and Data Collector Account (FinOps Center Account).
To create your SSL Certificate for your Front End Application Bucket that will be used in CloudFront Distribution, navigate to AWS Certificate Manager and Request a Certificate
Add the Domain for the FinOps Center Applicatoin and select the DNS Validation
Save the CNAME name and CNAME Value
Logi into Route 53 Account (likely Management Account)
Navigate to your Hosted Zone and Create a new A Record
Add the DNS Entries to the subdomain from the what was saved and the Value to Validate the SSL Certificate.
In approxiately 5 to 10 minutes the Certificate in the FinOps Center Account will show as Validated and able to be added to Distbitution.










Each Release has the Features in the Release the CloudFormation Script to use with the Marketplace AMI.
Navigate to the Release of your FinOps Center
Functional:
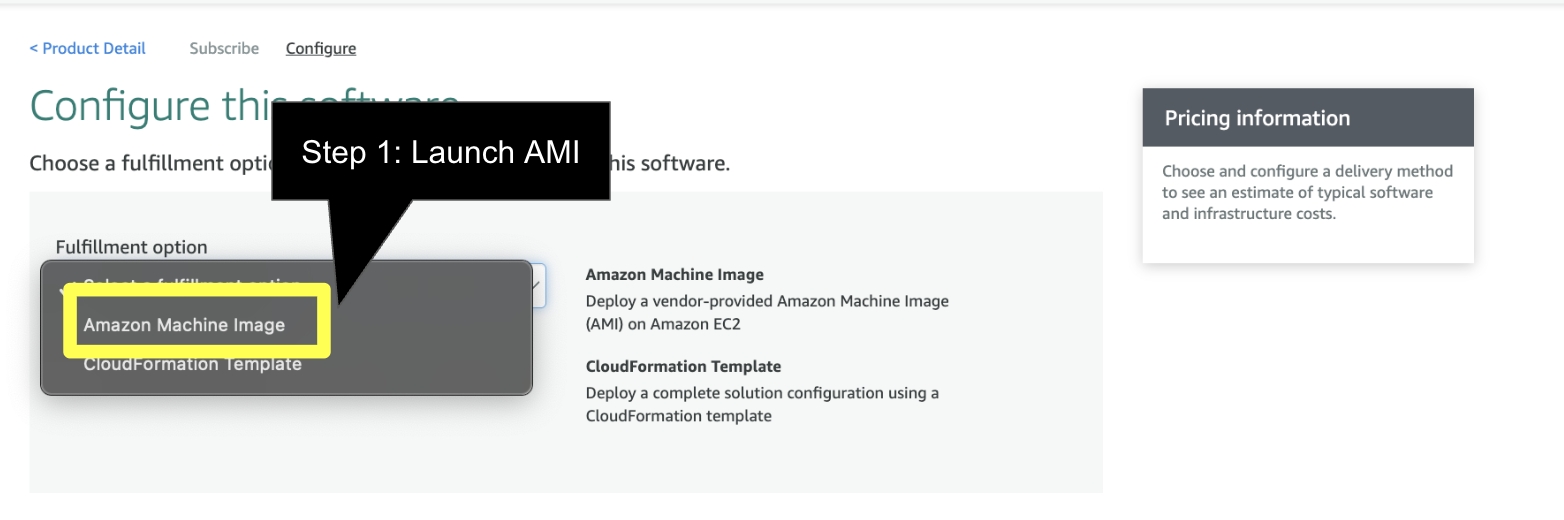
Release 25.2.0 is primarily around the inclusion of the Amazon Q in QuickSight Framework with UI Updates and Changes the CUDOS Framework embedding from Anonymous to User-Based.

FinOps Center's Installation Components
The installation of FinOps Center requires configuring your AWS Cloud Estate within the Management Account and the Delegated Admin Account or Data Collection where the application will be installed.
Pre-Requisite Task (~1hr)
Tasks in Management Account
Create Cost and Usage Report via Data Exports - via CID Framework
Create S3 Bucket for Cost and Usage Report - via CID Framework
Create IAM Role for S3 Bucket Replication - via CID Framework
S3 Management setup of Bucket Replication and Batch Operation (optional)
Enable Delegated Admin Account (suggest configured via AWS Organizations, Security Hub, or IAM Identity Center).
Assess Requirement
Admin - creating IAM Role
Tasks in Designated Admin/ Date Aggregation (~1hr)
Create Target Bucket for the Cost and Usage Report via Data Exports - via CID Framework.
Create S3 Bucket for Bucket Replication and Frontend Application
Configure S3 Buckets with CloudFront
Launch and Configure QuickSight
Access Requirement
Admin as the CFT create IAM roles
FinOps Center may take ~8 Hrs to load all Cost and Usage Data and 1 Day for Cost Recommendations.
The New Account Onboarding Process for FinOps Center is facilitated by access to the Account Management API in the Management Account. Within an AWS Cloud Estate, one account can be configured to be Delegated Admin and is the account FinOps Center is installed.
Steps to Create Delegated Admin if not created
Creation of New Account - Customers are advised to create an account (if not existing already) that requires Delegated Admin privileges, particularly for services like Security Hub and Systems Manager. While the naming convention is flexible, this account is referred to as the CloudOps Account by Cloud Scal3.
Enablement via Security Hub- Follow the instructions provided for enabling an account to be delegated Admin via Security Hub Setup. This involves configuring the Delegated Admin Account through Security Hub.
By following these steps, the integration for Account to Budget onboarding through FinOps Center is facilitated efficiently and securely.
FinOps Center Front End Application is deployed to and is served from S3.
Navigate to S3 and Create a new S3 Bucket in US-East-1 (N. Virginia)
Upon navigating to CloudFront, create a new distributions.
Updated for new AWS UI
Create a name for your Distribution and Add your cusotmer Domain. Note: it will try to validate the URL but select Skip for Now.
Level the S3 Selection and Select the Browse S3
Select your bucket and Select Choose
Leave the Origin Path to Default and Select Next
Do not Create a WAF and Select Next
Create Distibution
With the Distbituion Create we will need to Edit the Settings
In the Setting we are going to add the Domain Name of the application and select the the SSL Certificate that was created for it
In the Behavior Setting Update to have all Traffic to be Redirected to HTTPs
Ensure to update the specified settings below, unless instructed otherwise, while leaving the rest as default.
Update Viewer
9. Navigate to the S3 Bucket for FinOps Center Application and to Permission. Edit Permission with the Policy from CloudFront
A
Navigate to Route 53 or Domain Controller and Create an A Record that is Domain Name of your distribution
Create A Record
Example of CloudFront Distibution
Prior to starting the installation of FinOps Center, customers must understand how their company is organized by Roles and Organizational Naming.
Roles
During the installation of FinOps Center, the Role Names are created in Amazon Cognito. The functionality of the Roles is independent of the naming but will help if they are align to your organizational naming.
Default Labels for Roles
Admin
Technical Team Member that will be responsible for Setting up FinOps Center, Adding AWS Accounts, and Claiming Resource to Workloads.
Vendor Manager
Procurement, Finance, or Business Leader that manages discounts and buying decisions of AWS.
Financial Admin
Configured During FinOps Center CloudFormation Template
Organizational Naming is aligned to how customers Chart of Accounts are constructed. Organizational Naming can be update once a year aligned to your Creating of an annual budget.
Organization Naming is set via the Budget Creation Process which occurs via a csv upload or via the Budget Screen. The Organization Naming will be visible throughout the FinOps Center application and will need to be implemented in the Amazon Q in Quicksight Topics (if changed).
Default Organization Naming
Organization Naming
When creating Budget, you will be ble to provide Orgnaization Naming in the Create Budget.
Release 25.6.0
Updated Admin Screens for Financial Admins for Account Allocation
Update Month Close to run Final Cards based on seeing Invoice Number to Run Final Cards vs Manual Running Cards once Invoice is Recieved
FinOps Center is major Update with new User Experience and the integration of Cost Optimization Hub Approval Process.
While the prior UI was simplier that the AWS Console, we thought we could do better and are very happy to launch the New UI in 25.8.0.
The New U1 continues to have both Light and Dark Mode.
Another Major enhancement is the Process that leverages AWS Cost Optimization Hub Data Exports.
Workload Resource Start Date
To assist users identify Workload Resource for Claiming for Workload and/or specialized MAP Workload, Resources will have Start Date. Note: this capability will identify Resource Start date from Day 2 or FinOps Center installation.
This is the initial Release of Amazon Q in QuickSight FinOps Center Framework
Topics Created
AWS Product
AWS Portfolio
AWS Department
(We recommend that you keep instances with previous AMI until the upgraded installation is confirmed to be working properly. If recovery is required - you can restart the EC2 instance with the prior AMI which will update the CDK bucket with that version. Follow below instruction.)
Marketplace customers will receive an email that their is a new version of the FinOps Center AMI available. The AMI will be available in their EC2 Console for launch leveraging the same IAM Profile used during initial installation. The launched instance will update the FinOps Center cdk bucket with the updates. Select the FinOpsCenterStack.template.json and update the CloudFormation Stack with the object URL.
Click to Zoom
Click to Zoom
Validate the Parameters and advance through the next few screens and hit update.
To accelorate Environment Setup, your Cloud Engineer can navigate to the Step Functions in the AWS Console.
Select the CURProcessingStateMachine
Add the above once the Start Execution has been selected
During installation, default Lamda Limits are set for 3008MB.
Targeted Lamda Function to increase
UsagesLambdaHandler
UsagesLambdaHandler
FinOps Center is designed to have 2 tiers of allocation to a Financial Budget.
Account Allocation: Aligned to the multi-account framework, AWS Account Billing is split by percentage allocation to a budget. The Allocation begins to either the Vending date of the Account or the 1st of the Previous Month. Allocation can be updated to the beinning of Period (aka weekly). All resources will be allocated to that budget at the % rate.
Workload Allocation: Product Owners create estimates for Workload. Workload can then "Claim" resources to them by Admin, Financial Admins, or the Product owners that will then have 100% allocation to that budget as of the next day from Claiming.
As detailed below - Spending is then discounted (if applicable) and reduced by available Credits at the budget level.
FinOps Center onboards AWS Accounts via the Account Management API that is connected to AWS Organization when installed in the configured Delegated Admin Account.
When a new Account is Vended the Financial Admin, VM, or Cloud Engineers and Add the new Account by Checking for New Account.
Accounts can be additionally Onboarded when they show on the Cost and Usage Report.
As new Workload are added to Budgets, Monthly Schedules will need to be updated through a 2 Step Process.
First there is a Request to Reschedule the Budget by the Product Owner.
Amazon Q in QuickSight Backend Framework
Amazon Q in QuickSight Topics Components
Create IAM Profile for FinOps Center Installation
Subscribe and install FinOps Center Marketplace offering
Launch EC2 to copy FinOps Center code to S3 Bucket
Install FinOps Center from CloudFormation
Setup Amazon QuickSight and CID Framework
AWS Business Unit
AWS Spending
AWS Vendor
DataSet Created
FinOps_Center_E1
FinOps_Center_E2
FinOps_Center_E3
FinOps_Center_E4
FinOps_Center_Full
Resource View
finopscenter_period

FinOps Leadership that will be responsible for adding budgets, adding users to budgets, mapping aws accounts to budgets, adding AWS Credits to budgets, and all Month Close Activieis
BU_Manager
BU Manager is a Business/Finance Role responsible for AWS Spending within a Business Unit.
Department Manager
Department Manager is a Business/Finance Role responsible for AWS Spending within a Department
Portfolio Manager
Portfolio Manager is a Business/Development Role responsible for AWS Spending within a Porfolio of Products that actively manages budgets and cost governance processes.
Product Manager
Product Manager is a Business/Development Role responsible for AWS Spending within a Product(s) that actively manages workloads, budgets, and cost governance processes.



















Business Unit Owners can manage one or multiple BUs.
View
Application
Financial Scope in Business Unit(s)
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Spending - Business Unit
Daily Activities
Monitoring Spending to Budgets
Weekly Activities
Monitoring Spend Approvals
Monthly
Download FP&A Files for Business
FinOps Center is licensed under the terms and conditions of the AWS Marketplace Standard Contract
FinOps Center creates IAM Roles and Policies. The Engineer deploying must have Administrative Privileges. (DO NOT INSTALL USING ROOT USER)
Upon Selecting Next you will be taken to the YAML form to complete the FinOps Center Installation.
Name Stack: No Requirements
Environment Parameter:
Bucket of CUR
Path to CUR Date - name/name/name/
Athena DB Created by CUDOS Framework
CUDOS will create cid_cur name
Table name based on CUR creation naming
Provide S3 Bucket for Frontend Application Install
Organization Roles
Define your Organization Role Names
Create your First Admin User and Email
Department Owners can manage one or multiple Departmentss.
View
Application
Financial Scope of Department(s)
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Spending - Department
Daily Activities
Monitoring Spending to Budgets
Weekly Activities
Monitoring Spend Approvals
For maximum accountability, customers need their budet owners and their management to actively manage their spending during the billing cycle with approvals in that cycle.
With FinOps Center, we introduce the capability for Spend Cards that are created at the end of ever period.
Spend Card are created every Monday during the billing month with the last Card being created when the Cost and Usage Report includes the AWS Monthly invoice number indicating that the Billing Cycle has been finalized.
FinOps Center stores data in DynamoDB and aligns to general practices of using DynamoDB for Storage and Security.
As with all data storied in DynamoDB, customers can chose to encrypt the data at rest with the default AWS Owned , AWS Managed, or Customer Managed Keys
Complete QuickStart and Create Business Requirements Document
Allocated AWS Accounts to Financial Budgets prior to adding users
Communicate to users that they will receive emails inviting them to FinOps Center but that they should wait a day to enter the application or they may not have their experience loaded
Add Users via the Admin Screen not the Cognito Interface
Allocation Users to their Financial Scope once the Accounts have been Allocated to their Budgets
Configure initial Amazon QuickSight Dashboard to all Roles
Upload Customer logo prior to adding users
Update the Cognito Email Invites Prior to sending invites
Once the Customer Logo has been upload - create a new invalidation in CloudFront.
Validate that CloudFront is Configured Correctly.
Add Memory to Highly Used Lambda Function - UsageLambdaHandler
All FinOps Center APIs are managed by Cognito
Amazon Cognito Federated Identities issue short-lived AWS credentials using STS under an IAM role.
Amazon Cognito User Pools issue JWT tokens that are used to authenticate AppSync requests.
Because Cognito-issued credentials are automatically rotated and expire frequently (typically after 1 hour), long-term key rotation is not required for day-to-day operations.
Fault Conditions during installation will be discovered during the CloudFormation Template deployment.
If there is an issue during installation, CloudFormation will provide Root Cause Analysis.
Common Fault Conditions
Wrong Path to Cost and Usage Report
Cost and Usage Bucket was not created in US-East-1 causing S3 Bucket Notification Error
Wrong S3 Bucket name for installation of Front End Bucket
If a re-installation, prior deployed resources have not been delete fully
The initial Admin user will receive the initial email to begin to onboard users to FinOps Center.
The Recommended approach is to Create an Initial Financial Admin users and one Product Owner to assist with populating the installation with data.
From the Business Requirements, the Financial Admin can create the Organization Naming from configuring the Budget Screen or via CSV Upload.
Additional Post Installation Steps include updating the application with your company's logo and customizing the Amazon Cognito Welcome Email.
Product Owners need to own their Monthly budgets that are scheduled from their Annual Approved AWS Budgets. Working with their Portfolio Management, their Monthly Budgets will be Accepted so that all Users understanding spending within the expected Spending Run Rate.
Monthly Budgets, can be updated via the Rescheduling Process.
All Cloud Scal3 products are reviewed by AWS via their Foundation Technical Review.
FinOps Center is aligned to Customer Deployed Solution that requires that Customer Guidance is provided aligned to AWS Best Practices and are detailed in the subsection of the category.
Additionally our AWS Marketplace products are validated by the AWS Marketplace Onboarding team that both scans the AMIs that we upload and validate that our CloudFormation template adhere to their standards.
{
"source": "scheduler",
"timestamp": {
"props": {
"inputPath": "$.time"
}
}
}Updated Budget Screen for all Users
Adding Resource Launch Date to Resource Table to assist with Workload Allocation



FinOps Center creates IAM Roles and Policies. The Engineer deploying must have Administrative Privileges. (DO NOT INSTALL USING ROOT USER)
Upon Selecting Next you will be taken to the YAML form to complete the FinOps Center Installation.
Name Stack: No Requirements
Stack Parameter:
Bucket to CUR - cid-(CUSTOMERDELEGATEDADMINACCOUNT)-data-exports
Path to CUR Date - cur2/CustomerManagementAccount/cid-cur2/data
Athena DB Name - cid_data_export
Athena Table Name - cur2
Athena DataCalog - AwsDataCatalog
Athena WorkGroup - primary
Roles aligned to Busienss Requirements
Enviornment Parameters
Static Website - S3 Bucket Name Created for Frontend Bucket
From CloudFront - Distribution Name
Create your First Admin User and Email
Cost Optimization Hub
Bucket to CUR - cid-(CUSTOMERDELEGATEDADMINACCOUNT)-data-exports
Path - coh/(CustomerManagementAccount)`/cid-coh/data/
FinOps Center Enterprise (Annual or Monthly)
FinOps-In-a-Box (Annual or Monthly)
FinOps-in-a-Box (Hourly)
Upon complete the configuration to your AWS Environment (QuickSight) you will navigate to the Amazon Q in QuickSight Marketplace offering and subscribe to the services
Upon Subscribing the page, will refresh to add the AMI
Click the Continue to Configuration and Select the AMI
Select your Version and Region and select Continue to Launch
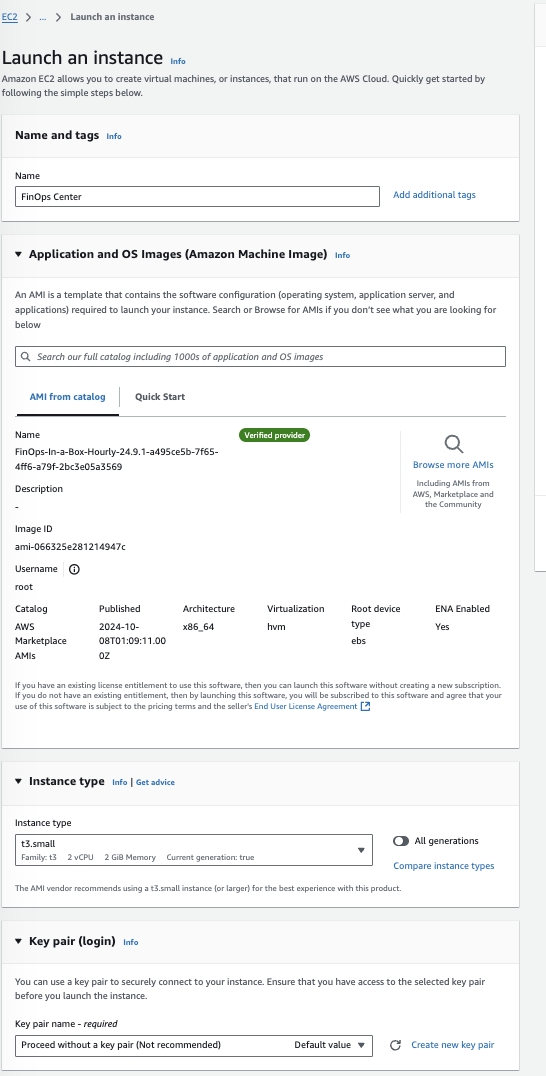
Launch via EC2
Add the name of the Instance, Select no Keypair
Add the Launch Profile from the FinOps Center Installation and Launch Instance
Customers can update the header and login logo in the FinOps Center implementation
Customers' logo needs to have the file name customer-logo and format svg. (if you have image in different format they must be converted to svg.)
The logo gets uploaded in the s3 bucket of the frontend application in the root directory.
Product Owners will navigate to their Budget Page and select the Product Budget that they want to schedule.
Within the Budget, Complete Schedule
Once Schedule is Completed, Product Owner Submit for Approvals and see the Budget Status as Pending.
Financial Admins are the primary managers of the AWS Cloud Estate.
View
Application
None
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Vendor, AWS Spending
CUDOS
Daily Activities
Add/Manage Users
Add initial AWS Account Allocation to Budgets
Claiming/Unclaiming Resources to Workloads
Adding QuickSight Dashbaords/Topics
Weekly Activities
Monitoring Spend Approvals
Monthly
Close Month
Download/Upload AP and FP&A Files
Business Unit Roles have access to all spending data within the Business Unit(S) the have Financial Scope. Within Budgets Tables, their visuals are layered and can be navigated down to the Monthly Schedule per Budget.
The Page can be toggled Monthly vs Annual with all visuals updating on selection. The Heat Map Chart on the left scales to the contribution of total spending across the financial scope with the color representing spending to budget. If area is Gray, that individual budget is not approved.
FinOps Center Users are onboarded to the application by Admin Users. All users are stored in Amazon Cognito that accepts mass uploads. (contact support for assistance).
The Admin Configuration Screen is accessible to the Admin User that is created during the installation of FinOps Center. Additional Admin Users can be created like any other role
Admin users are responsible for adding users with their roles. Those Roles can be updated. Each users requires an unique email address. (+email are Supported)
To assist with the user experience, we recommended that Filter Null Values are created for the Service and Product Family Services within each Topics Data Configuration
To assist the Quick Sight Topic understand how business weeks are defined, each topics needs to have a Custom Instruction
Customer Instruction
Week are defined by sunday to saturday. the first week of each month starts the 1st of month to saturday 23:59. The last week of the month starts Sunday 00:01 to the last day of that month. Normal weeks are sunday to saturday.
When Forecasting only show the past 2 months and then the forecast for the selected time
Agent Bill for Amazon Q in Quicksight was built considering the challenge for Row Level Security. Each Role has their Athena Queries, QuickSight Datasets, and QuickSight Topics.
The Dataset are configured with User-based rules leveraging FinOps Center User table for Financial Scope. Users Scope is updated when the Dataset's SPICE is Refreshed.
Users see their Data in Scope of their Users Allocation of Accounts and Financial Budgets configured in FinOps Center.
In image below, FinOps Center users Products on the left are what are reflected in Embedded Amazon Q.
All Cloud Scal3 products are sold exclusively via the AWS Marketplace.
Any customerized offering or pricing is handled via the Standard Private Offers processes within Marketplace.
Financial Admins are the primary managers of the AWS Cloud Estate.
View
Application
All Financial Scope
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Vendor, AWS Spending
CUDOS
Daily Activities
Adding/modifying Budgets
Adding/modifying Users to Budgets
Adding/modifying AWS Account Allocation to Budgets
Adding AWS Credits to Budgets
Weekly Activities
Monitoring Spend Approvals
Monthly
Close Month
Download/Upload AP and FP&A Files
Roles and Users have Allocation/Visibility within their Financial Scope. The allocation is across all Tabs and within their Amazon Q Topics.
On the Summary Page, the Account Allocation for the User are shown Across Current, Expiring, New, Past, and Future.
For Financial Admin, Admin, Vendor Management, Business Unit Owner, Department Owner, and Portfolio Owners Accounts/Workload needs have a Workload Created by the Product Owner for it to be visible.
Budget Pages, Reporting, and Amazon Q Visibility will be defined on their Functional Page Documentation.
Agent Bill is the embedded Data Assistant to FinOps Center that leverages Amazon Q in QuickSight.
At the end of each Bill Period, Approved Spending needs to be integrated back to Core Financial Systems to both Pay your AWS Bill and Accrue Spending to Budgetary systems for FP&A or other KPI reconciliation.
To Create File, the Venofr, PO, Invoice, and Internal Memo must be complete.
FinOps Center generates the Account Payable Files for integration at the E1 Level (Default Business Unit). Note: Credits are applied for all of the Credits applied by AWS to your Cloud Estate within the CUR.
FinOps Center generates Budget level Accruals with Credits applied witihin FinOps Center.
As of FinOps Center 25.2.0, FinOps Center has 7 roles with specific Daily, Weekly, and Monthly Activies.
Product Owners own creating Workload Estimate in FinOps Center leveraging a AWS Pricing Calculating Link.
Any entity (internal user, AWS, AWS Partner) can create an estimate for a Workload via the AWS Calculator - https://calculator.aws/. Each Workload Estimate should be for the Workload in that AWS Account. Once the Estimate is created, the Product Owner will add the Link to the Estimate with the Monthly Estimate.
Once the Estimate is created, the Product Owner will add the Link to the Estimate with the Monthly Estimate and Save
Workload Estimates flow to the Budget Schedule to be included in Monthly Budget Schedule.
Agent Bill Amazon QuickChat FinOps Center provide Curated Topics for the different Personas/Roles with FinOps Center by their Financial Scope.
Agent Bill provides both the framework to extract data from customer's FinOps Center application and integrates it with the AWS Cost and Usage Data.
A submitted Budget will then be sent to the Portfolio User to Approve or Reject.
From their Summary Page they will see they have a Budget Task to take action.
From the Budget Page, the Portfolio Owner will be guided to the Budget Requiring Action.
Porfolio Owner select and Take Action to Approve/Reject Budget Schedule
Upon Approval, the Budget Card will show approved for both Product and Portfolio User.
Agent Bill Embedded Data Assistant is a solution that leverages Amazon Q in QuickSight embedded Q Bar for Registered Users.
Each FinOps Center Users is entered in the FinOps Center Users Pool then added as a QuickSight User with their Role.
User can ask any question around their spending aligned to the Financial Scope.
Users can Pin useful Question and Visuals for Ease of Use
Agent Bill leverages Amazon Q in QuickSight's Forecasting Algorithm to provide users expected spending aligned to their Financial Scope.
FinOps Center Enterprise
FinOps Center FinOps-in-a-Box
FinOps Center FinOps-in-a-Box Hourly
The Amazon Q in QuickSight FinOps Center Framework uses the same Deployment Model as FinOps Center via the Marketplace - AMI with CloudFormation.
Once the Offering is added to your AWS Accounts you will have an AMI that needs to be launch with the IAM Profile that was used for the Product Installation.
The Solution code will be deployed via 2 CloudFormation Scripts.
The First CFT builds and deploys the backend that will extract data from your FinOps Center application's DyanamoDB tables and pushes them to S3 that are created. Glue Crawlers then create the schema to be leverage for the 2nd CFT.
Note: Prior to proceeding to the 2nd CFT Script the Glue Crawlers must successfully complete and the new S3 buckets ( & ) must be shared with QuickSight.
The 2nd CFT will install the Athena Queries, QuickSight Datasets, QuickSight Topics, and other configurations. For the Installation, you need the Author Pro ID that was created to provide as a parameter for the Template to complete.
Once the AMI is launched and the code is deployed to your cdk bucket, you navigate back to the Configure Screen to install the CloudFormation Templates.
The First CFT to launch is the Amazon Q in QuickSight FinOps Center Backend Framework.
Continue to Launch Stack
Prior to Launch the 2nd Stack -> navigate to Glue and Validate that the Crawlers have run successfully.
Launch the 2nd Stack - Amazon Q in QuickSight FinOps Center Q Topics
On the 2nd Screen after launching you need to add the Author Pro that you setups within your QuickSight Environment
Once the Initial User Admin receives the Cognito Email they can create the initial Financial Admin User. Prior to creating user, its best practice to configure the Welcome Email in Cognito.
Add Users
Users Lists
Update User Role
Import via Cognito Console
As an alternative to adding Users via the FinOps Center Application, Admins can log into the Delegated Admin/Data Collection Account and navigate to Cognito->FinOpsCenterPool
Create Import Job
Finops Center provides your companies Core Cloud Financial Processes.
Financial Budget Onboarding/Modifying
Business User Onboarding
Financial Budget Mapping to User
Enterprise
FinOps-In-a-Box
Hourly
Agent Bill loads data to Quick Sight via Athena for each role. Depending on the number of refreshes that customer configure, there will be at least 6 queries each day of large datasets. Query results bucket should have a lifecycle rule that deletes bucket results every 30 days to avoid undue costs.
Adding and Managing AWS Credits can be very time consuming to FinOps teams. Customers are awarded credits aligned to a new AWS PoC or aligned to programs like the Migration Acceleration Program (MAP).
FinOps Center enables Financial Admins and Vendor Management to add Credits to be tracked for accrual at a Budget Level.
When a new Credit is available, the Financial Admin or VM add with the Credit information to FinOps Center
The Credit and Balance are available to users within Spaces and accounted for during the Month Close Process.
Upon considering to install the Amazon Q in QuickSight FinOps Center Framework please be aware of the following:
Lambda code hosted in your S3 buckets are not ingested nor scanned by AWS Marketplace. This creates an external dependency. Applications that require external dependencies on deployment must follow product usage policies which includes proper disclosure. In the Release Notes of each FinOps Center Release include the results of the AWS CodeGuru Scan.
FinOpsCenterQGlueCrawlerRole295A8956 : add a warning in your deployment guide, product access instructions, or clusters and resources long descriptions that customers should consider deploying into new AWS accounts because the permissions allow your application access to read, edit, and/or delete existing AWS resources in the AWS account.
To insure that their is oversight on Spending, Portfolio Owners need to Approve, Reject Accepted Cards and Resolve Rejected.
While Spend Cards are Open, Portfolio have no Action
Portfolio Owner need to Approve, Reject, or Resolve Submitted Spend Cards
Portfolio Owners can manage one or multiple Portfolios.
View
Application
All Financial Scope within Portfolios
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Spending - Portfolio
Daily Activities
You can add any QuickSight Dashboard to FinOps Center by adding the Dashboard ID and adding your application URL to the Embedded Dashboard management page. (Resticted to Financial Admin, Vendor Manager, and Admin Users.
In QuickSight, add the Dashboard to the Group you wish to view in FinOps Center
In the URL is the Dashboard ID for your QuickSight Dashboard
Add Dashboard ID to the Configuration Page in FinOps Center
Navigate to Reporting Page to View
Customer Support is initiated via cloudscal3.com (footer)
Support Tiers
Agent Bill Amazon Q in QuickSight for FinOps Center is installed with currated Topics that can be customized to your organizational naming convention.
Each Topics need to be Modified to your Organization.
Additional Hints to provide the best expereince for your Users
Select Non Additive for the Monthly Periods
Spend Cards are created every Monday. Each Product Owner will see their Cards to Approve or Dispute
Status will Change once Action is taken.
FinOps Center
To recovery FinOps Center the application and the database need to be restored to the last know functioning state.
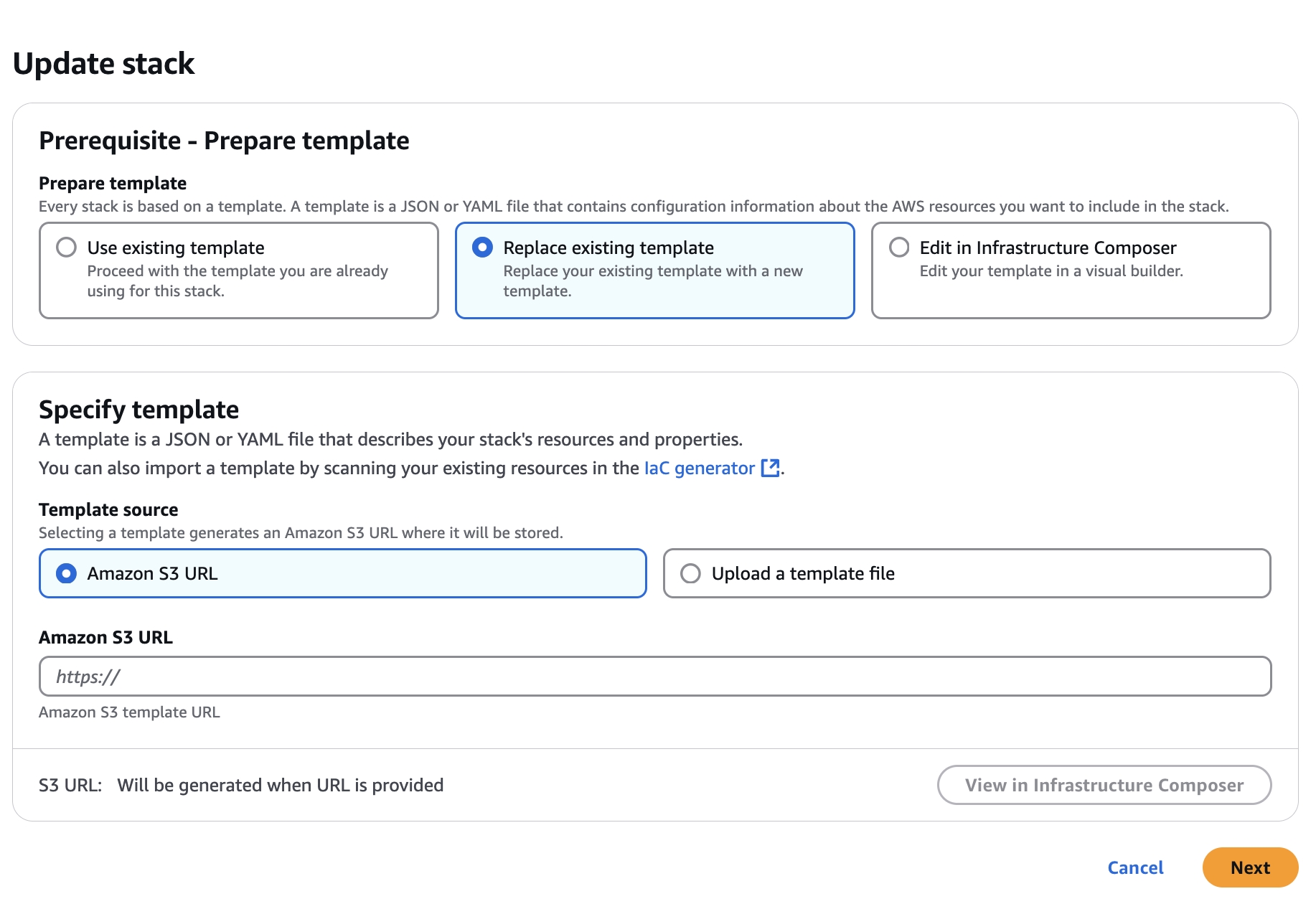
If their is an issue with the application after patching the environment with a new release, return to the ami of the prior release and launch instance. The cdk bucket will load with the previous release. Return to the CloudFormation and the stack with the previous releases JSON Object.
FinOps Center stores all of its data in DynamoDB. During the installation, the DynamoDB tables are enabled with Point-in-time Recovery. If any tables needs to be recovered, an engineer can log into the console, navigate to the DynamoDB service, and restore any table to the time of last operation.
RTO Target
FinOps Center RTO is plus 2 hours from your original installation time. This is based on a scenerio where your AWS Account has been compromised and you need to restore the DynamoDB tables from an S3 backup in a new CloudOps Designated Admin Account.
RPO Target
FinOps Center RPO is close to zero as the Cost and Usage Report will be created in the MaterPayer Accounts. Any budget mapping can be be restored from backup but it would cause any data lose.
FinOps Center budgets Rollup through Roles and User Based on their Financial Scope.
For Budgets to be shown with Variance they must have Status Approved.
The Product Budget Status show the Product Budget Status.
Additionally the Reporting -> Variance Report shows Variance by Product.
All AWS Accounts are at minimum allocated to 1 Financial Budget and define as an Account Type (Production, Pre-Production, Shared, Development or Sandbox). To complete mapping the total allocation must be 100%.
Accounts can be mapped to multiple budgets but need to have total allocation of 100%.
Allocation can be updated to a new start date and allocation
Select Remap to update account allocation and start date
FinOps Center S3, Lambda, and DynamoDB components like any other application via VPC Endpoints.
New VPC
1 VPC, e.g. 10.0.0.0/16
At least 2 public and 2 private subnets across 2 AZs
Management Users (Financial Admins, Vendor Management, Business Unit, & Department) can monitor the Cards in their Financial Scope with the capability to identify the Product and Portfolio Users that own the Card Approvals.
Product Owners can manage one or multiple Products.
View
Application
All Financial Scope within Portfolios
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Spending - Product
Daily Activities
FinOps Center maps Users to their Financial Budget/Scope. A key feature of FinOps Center is "Rollup" of Spending and Budget within the hierarchy.
As depicted below, the Roles rollup spending from the members of their Financial Scope.
From the Drop Down, A user will be added to the Financial Scope aligned to the Role they were onboarded to when they were added to FinOps Center.
Users can have multiple scopes within their hierarchy but must have the same "Parent". In the examples below Department can have multiple departments within Enterprise but not in different Business Units.
Business Unit Role
Department Role
Vendor Manager Role deals around Buying and Discounts Activities.
View
Application
All Financial Scope
Amazon Q in QuickSight Topics / CUDOS Access
Topics: AWS Vendor, AWS Spending
Adding QuickSight Dashbaords/Topics
Monitoring Spending to Budgets
Approves/Ignore Cost Recommendations
AWS Account to Budget
Resource to Workload to Budget
Release Resource
Rollup Allocation/Visibility
Estimate to Budget
Budget Scheduling
Create Schedule
Approve/Reject Schedule
Request Reschedule
Approve Reschedule
Rollup Budgets
Period Spending Cost Governance
Cost Optimization Approvals
AWS Credit Allocation
Close Month
AR File
FP&A
The Role AmazonQFramework-FinOpsCenterQGlueCrawlerRole* leverages the Glue Services Role that enables the solution to Access additional resources than the scope of Amazon Q in QuickSight FinOps Center. If this is an issue, consider deploying in stand alone AWS Account.
AWS Marketplace Scans the AMIs that Cloud Scal3 Provides but not the Code Artifacts that are used during the installation. Please view the results of our internal code scanning with AWS CodeGenius with the version Release Notes that you are installing.
Approve/Reject Budget Schedules
Weekly Activities
Approve/Reject Spend Cards Submissions
Create/Modify Budget
Create Workload
Claim/Unclaim Resources
Weekly Activities
Approve/Reject Spend Cards
Daily Activities
Adding/Modifying Discounts
Adding/Modifying Budgets
Approves/Ignore Spending Recommendations
Weekly Activities
Monitoring Spend Approvals
Agent Bill → AgentCore MCP Gateway connectivity
AgentCore Observability Console Health Endpoint (/health)
AgentCore ECS Runtime
ECS task status + ALB target health
FinOps Center Lambda functions
CloudWatch Logs & Lambda Insights
AppSync API layer
AppSync console resolver metrics (4xx / 5xx / latency)
DynamoDB, S3, Secrets Manager
CloudWatch Service Metrics
All FinOps Center DynamoDB Tables that get deployed are configured with Point in Time Recovery.
Agent Bill
The data that Agent Bill accesses are FinOps Center tables that follow the same recommmednations for Recovery. Recovery of the solution is via a reinstall via CloudFormation Scripts.





























































FinOps Center is deployed entirely within customer’s AWS account and is built 100% on native AWS services, enabling centralized operations management, governance, and observability aligned with AWS best practices. It provides customers with full ownership and control of their operational environment while supporting scalable, secure, and compliant centralized management across their AWS workloads.
Centralized Operational Control
The solution is designed to support centralized visibility and control through seamless integration with AWS native tools, allowing customers to centrally manage infrastructure, security, and operations. Key components include:
AWS CloudFormation: FinOps Center serverless infrastructure and application code is deployed with CloudFormation, ensuring consistency of deployments.
AWS Control Tower and AWS Organizations Alignment: FinOps Center integrates with the Account Management APIs that are accessed from the Delegated Admin account enabling onboarding of new AWS Account immediately vs when the account appears on the Cost and Usage Report
Centralized Monitoring and Logging
To support operational excellence and proactive issue detection, the solution integrates natively with:
Amazon CloudWatch (Logs, Metrics, Alarms, Dashboards): All FinOps Center operations are monitored by CloudWatch, which provides real-time performance monitoring and unified observability across application components.
AWS CloudTrail and AWS Config: Aligned to AWS Best Practices, all FinOps Center transactions and configuration updates are tracked with AWS CloudTrail and AWS Config.
Centralized Compliance and Governance
The solution promotes centralized compliance through:
AWS Config Rules and Conformance Packs: Evaluate resource configurations continuously across all regions and accounts to ensure compliance with internal policies and industry regulations.
IAM, SCPs, and Resource Policies: Secure access to resources is managed centrally using AWS IAM policies, permission boundaries, and Service Control Policies (SCPs) where AWS Organizations is used.
Privacy Policy for Cloud Scal3 Inc.
Last Updated: October 24, 2024
At Cloud Scal3 Inc. (“we,” “us,” or “our”), we value your privacy and are committed to protecting your personal data. This Privacy Policy explains how we collect, use, and safeguard the information you provide when visiting our website, [www.cloudscal3.com](http://www.cloudscal3.com), and www.finopcenter.com or interacting with us.
1. Information We Collect
We may collect and process the following types of personal data:
- Contact Information: This includes your name, email address, phone number, and any other contact details you provide. - Usage Data: Information about how you interact with our website, such as IP address, browser type, time zone, referring/exit pages, and clickstream data. - Marketing Data: Information about your preferences and interests, which may include responses to marketing campaigns or surveys you participate in. - Cookies and Tracking Technologies: We use cookies and similar tracking technologies to enhance your experience, understand your preferences, and deliver targeted advertisements.
2. How We Use Your Information
We use the information we collect in the following ways:
- To Improve Our Website: We analyze data to understand how visitors use our site, ensuring it is easy to navigate and tailored to user needs. - To Communicate with You: We may use your contact information to send you promotional content, newsletters, updates, or respond to your inquiries. - For Marketing Purposes: We use your information to provide personalized advertisements and special offers based on your interests, either through our website or third-party marketing partners. - To Comply with Legal Obligations: We may process your data to comply with legal requirements or respond to legal requests.
3. Sharing Your Information
We do not sell your personal data. However, we may share your information with:
- Service Providers: Third-party vendors who assist us in providing website functionality, marketing services, analytics, and other business operations. - Advertising Partners: Marketing agencies and advertisers to help deliver tailored content and ads that may interest you. - Legal Authorities: When necessary to comply with legal obligations, prevent fraud, or protect the rights of Cloud Scal3 Inc. and others.
4. Data Retention
We retain your personal data only as long as necessary to fulfill the purposes outlined in this policy, or as required by law. You may request deletion of your data by contacting us at [insert contact email].
5. Your Privacy Choices
You have the following rights regarding your personal data:
- Opt-Out: You can opt out of receiving marketing communications by following the unsubscribe instructions in the emails we send or contacting us directly. - Access and Correction: You may request access to, correction of, or deletion of your personal data by contacting us. - Cookie Preferences: You can manage your cookie settings through your browser or our cookie consent tool.
6. Security
We implement appropriate technical and organizational measures to protect your personal data from unauthorized access, loss, misuse, or alteration.
7. Changes to This Privacy Policy
We may update this Privacy Policy from time to time to reflect changes in our practices or legal requirements. We will post any updates on this page and notify you of significant changes through our website or other communication channels.
8. Contact Us
If you have any questions about this Privacy Policy or our data practices, please contact us at:
Cloud Scal3 Inc. Email: [email protected]
Cookie Policy for Cloud Scal3 Inc.
Last Updated: October 24,2024
Cloud Scal3 Inc. ("we," "us," or "our") uses cookies and similar tracking technologies to enhance your experience and analyze how our websites, [www.cloudscal3.com](http://www.cloudscal3.com) and [www.finopscenter.com](http://www.finopscenter.com), are used. This Cookie Policy outlines how we use these technologies for marketing purposes.
1. What Are Cookies?
Cookies are small text files stored on your device when you visit a website. They help us remember your preferences, understand how you interact with our websites, and provide tailored content, including personalized marketing messages.
2. Types of Cookies We Use
We use the following types of cookies on our websites:
- Essential Cookies: These cookies are necessary for the operation of our websites and enable features like secure login and form submissions. They cannot be disabled. - Analytical/Performance Cookies: These cookies help us understand how visitors use our websites, which pages are popular, and how we can improve site performance.
- Marketing/Advertising Cookies: These cookies track your online activity to deliver personalized ads relevant to your interests. We use these cookies to analyze user behavior and ensure our marketing efforts are effective.
- Third-Party Cookies: In some cases, we use third-party service providers (e.g., advertising networks, analytics services) that set cookies on our behalf to deliver tailored advertisements and analyze website traffic.
3. How We Use Cookies for Marketing
We use cookies to:
- Understand User Preferences: We track how you interact with our websites to understand your preferences and deliver personalized marketing content. - Display Targeted Ads: We use marketing cookies to deliver relevant ads on our websites and other platforms based on your interests and browsing behavior. - Measure Campaign Effectiveness: Cookies help us analyze the performance of marketing campaigns to optimize our advertising efforts.
4. Managing Your Cookie Preferences
You have the right to manage or disable cookies. Here’s how:
- Cookie Consent Tool: You can manage your preferences through the cookie consent tool that appears on our websites when you first visit or by clicking on the “Cookie Settings” link available on our website footer. - Browser Settings: You can adjust your browser settings to refuse cookies or delete existing cookies. However, this may affect the functionality of our websites. - Opt-Out of Targeted Advertising: You can opt out of personalized advertising by adjusting your preferences on advertising platforms or using industry opt-out tools like the [Network Advertising Initiative](https://www.networkadvertising.org/) or [Digital Advertising Alliance](https://youradchoices.com/).
5. Data Protection and Privacy
Cookies may collect personal data, such as IP addresses or unique identifiers, to tailor marketing efforts. For more details on how we handle personal data, please refer to our [Privacy Policy](#).
6. Changes to This Cookie Policy
We may update this Cookie Policy periodically to reflect changes in our practices or legal requirements. We will notify you of significant changes through our websites or other communication channels.
7. Contact Us
If you have any questions about this Cookie Policy or how we use cookies, please contact us:
Cloud Scal3 Inc. Email: [email protected]
With Marketplace Subscription
Business Critical
Direct Customer Success
<2Hrs during EST Business Hours 8AM-6PM
Contact Sales
Tier
Method
SLA
Pricing
Free Trial
Blogs
N/A
Free
Subscription
Emails and Web
<8Hrs during EST Business Hours 8AM-6PM
The CFT will take about 3 minutes to Run but the deployment will still be running. Allow for 15 mins before returning to the Back to QuickSight Console. In Console, navigate to the Groups Tag in Management to add the Author Pro User to the Topics-Admin Group.
Navigate to the Author Pro's Console and monitor the Topics being built. Note that Topics are built once the SPICE for the Dataset has successfully been Refreshed. Depending on the amount of data in your CUR2 or Application, this can take up to 30mins. As Topics appear they will be automatically added to the application by Role. As a best practices, run an invalidation in CloudFront upon completetion of all Topics being created.

The installation of the scripts will take approximately 10 mins but the Lambda function that create the Athena Queries/Views, QuickSight Datasets, SPICE loading, and Topics can take upto 30 minutes.




In the provided csv, complete rows:
L for Customer Role of User
N for Email address of User
O for Email Validation to True
V for the Username for FinOps Center








NAT Gateway(s) in public subnets
Route tables:
Public subnets → 0.0.0.0/0 via IGW
Private subnets → 0.0.0.0/0 via NAT
Attach FinOps Center Lambdas to the VPC
For each Lambda that should live “inside the VPC”:
IAM for VPC attachment
Add the managed policy AWSLambdaVPCAccessExecutionRole to the Lambda execution role so Lambda can create Hyperplane ENIs
Attach Data
S3 Gateway – for CUR 2.0, Cost Optimization Hub exports, Athena query results
Interface endpoints (AWS PrivateLink) for:
com.amazonaws.<region>.dynamodb
...sts
...logs (if you want private delivery to CloudWatch Logs)
...secretsmanager / ...ssm / ...lambda as needed
Attach security groups that allow inbound from sg-finopscenter-lambda (or ECS SG) on 443.
Product Owner
All users mapping can be remapped(adding or subtracting) by selecting the user from the list ->
and adding the new mapping



FinOps Center leverages AWS Cost Optimization Hub(CoH) Recommendations via Data Exports. CoH Data is integrated into FinOps Center and made available to Finance CCoE and Vendor Management Users to Approve or Ignore the Recommendations with Top Optimizations presended on Summary Page.
Financial Admins and Vendor Management make Approval and Ignore decisions on which Recommendations are to be Implemented by Cloud Engineers.
Cloud Engineers view the Recommendations that they are to take action on and then Mark that the Approved Recommendation has been taken action on and then mark as Implemented.
Workload allocation begins with the Product Owner creating an estimate for their workloads. Within Space, Product Owners will navigate to a Budget within their Scope and Select the AWS Account where the workload will be created.
Workload need to be named, have an AWS Pricing Calculator, and a Launch Date(Month). If there is a targeted Teardown for the workload enter the End Month. By default, Estimates will end a year of year.
Once Estimates are created Product Owners, Financial Admins, or Admins can Claim Resources to the Workload within the Resource Tab.
On load, Resource that are Open to be Claimed will be visible in the table. Users can use the search to identify by Service Name, Resource Name, or Tag.
Claiming Resources can be done across multiple Workload or Multiple Resources can be Bulk Claimed.
Multi-Workload
Bulk Claim
To view Claimed Resources, Select the Claimed Resource Checkbox. The Status visual provides information on which Budget it belongs , the date of action, and the User that made the action.
For Claimed Resources within the Budget Scope, the Resource(s) can be Released back to the available pool to be Claimed by another Workload or to Account Allocation.
Agent Bill Amazon Q for QuickSight For FinOps Center brings the power of Amazon Q to your FinOps Users.
To be able to be installed, Customers need to have one of the FinOps Center versions installed, have FinOps Center Minimal Setup Complete (See Below), and have Amazon Q in QuickSiight enabled in there environment with at least 1 Author Pro Enabled with Embedding of your FinOps Center application configured.
FinOps Center Minimal Setup for the Amazon Q in QuickSight Framework:
One Product Owner Onboarded
One Budget Onboarded and Mapped to Product Owner
One AWS Account Mapped to Budget
One Workload Created to the Mapped AWS Account
One Resource Claimed to the Workload
All FinOps Center underlying compute (including Amazon Q in QuickSight) is the responsibility of Customers.
Pricing for Amazon Q in QuickSight - A $250/month per account Amazon Q enablement fee applies for accounts with at least one Pro user or with at least one Amazon Q Topic.
Click to Zoom Click to Zoom
To Install Agent Bill Amazon Q in QuickSight for FinOps Center customer must Add 1 Author Pro User to their QuickSight Environment.
Embedding must be enabled with the url of the FinOps Center Application.
Financial Admin and Vendor Manager Roles have access to all spending data. Within Budgets Tables, their visuals are layered and can be navigated down to the Monthly Schedule per Budget.
The Page can be toggled Monthly vs Annual with all visuals updating on selection. The Heat Map Chart on the left scales to the contribution of total spending across the financial scope with the color representing spending to budget. If area is Gray, that individual budget is not approved.
Below the Top Visual are the individual Business Units Spending. To drill down on a Business Unit Select the Details of the Departments
Each Department is visible within the Business Unit with the ability to view Portfolios within that Department
Each Portfolio shows all of the Product Budget with the corresponding Monthly Schedule including the cumulative Workload Estimates.
FinOps Center has a low burden on Technical Operations Teams once the pre-requisite AWS components are configured and the Application is deployed.
Skills of the Technical operations Team:
AWS Engineering with specific understanding of the S3 Bucket Replication, CloudFormation, VPC Configuration, and Web Application Management leveraging CloudFront.
AWS Data Engineering with understanding of DynamoDB Backups to S3
Account Vending Process with Tools like Control Tower
Operational Checklist to Validate Functional Application
Validate that Cost and Usage Report has replicated to the Cloud Operations Account Bucket.
Compare loading of the Application Updated (Note: The application time stamp should be approximately 1 hr after the Bucket timestamp. This is due to the allowance of “eventual consistency” of bucket replication).
The Finance and Business Teams are the primary users of FinOps Center and will need to be enabled in operations of the applications. In the Finance and Business Teams, there should be members that are comfortable in the development of QuickSight Dashboards and how to share information to the Technical Operations Team to make a Dashboard available to different Roles.
The Finance and Business Team are the key to driving spend accountability with FinOps Center. They must daily monitor spending, card approval, and account mapping to validate that users are acting on the data.
AWS Multi-Account Framework
AWS Control Tower with Multi-Account Strategy
AWS Cloud Financial Management
Cognito Quotas
DynamoDB
Lambda
DynamoDB
Encryption
Monitoring
Backup
Lambda
Security
Monitoring
VPC Endpoints
IAM Best Practice
Amazon Q in QuickSight Community
Cloud Intelligence Dashboard Framework
Creation of Approved AWS Spending by Budget
FinOps Center manages Financial Budgets that have been approved by customer's Core Financial Budgeting process. The Financial Budgets can be onboarded to FinOps Center via the Application UI or by uploading a CSV files.
FinOps Center Roles - Financial Admin & Vendor Manager (Default Roles)
Navigate to the Vendor Manager
Via Site
Define Organizational Naming for the Year
Add Line Item
Via CSV
The CFT for the Backend Framework Setup and the creation of the QuickSight components create IAM in the AWS Account that it is installed.
Below is the list of the Roles and their Purpose:






















Sample File:
File Name
The Chart of Account File should be generated from your Core Accounting System that reflects your Hierarchy and Approved Budget Spending for AWS.Budgets (via file format) can be updated based on Customer requirements.
Customer_2025_true_2025-11-01_false_Budget_v1.csv
2025
effectiveYear - sets endDate to 2023-12-31. If isNew = true, startDate will be overridden to 2023-01-01
true
isNew - sets startDate to effectiveYear-01-01 and reloads the budgets
2025-11-01
startDate - sets when the budget becomes active. Must be 1st of month
false
isOverride - if you want to replace the existing entries, clears the database for given effective year and creates new entries
Customer Option
None
v1
None
I am a CCoE User and I want to create a New Budget for All Project for the New Budget Year.
I am a CcoE User and I want to up to update a Product’s Annual Budget on 7-01-XX
I am a CCoE User and I want to add a New Product and it’s budget
Chart of Account Integration
Admin users upload the Chart of Account File in the Configuration Page. The Chart of Account File is uploaded in the *.sorfile s3 Bucket and processed by Lambda into DynamoDB.
Invoice Integration
CCoE and Business Unit Users will be able to download csv to their desktops for integration into Core Financial and/or FP&A Solutions.




Lambda to update config in s3 bucket
Lambda to setup quicksight assets
Lambda to execute named queries on athena
Lambda to check quicksight dataset refresh status
Lambda to create and database on athena which connects to s3
Lambda to create datastores, datasets, themes on quicksight
Lambda to create datastores, datasets, themes on quicksight
Lambda to create topics on quicksight
IAM Execution role to Extract Data from DynamoDB Tables
Lambda to write data into s3 bucket
Lambda to read data from dynamodb tables
Lambda to setup glue crawlers

Launch through EC2
Click to Zoom
Click to Zoom
Configure Instance to your companies standards. As note previously, the EC2 instanced provisioned is used to copy files to S3 for the FinOps Center deployment. We recommend a small instance (T3 Small) be used and can be shut down once the files are copied to S3.
Click to Zoom
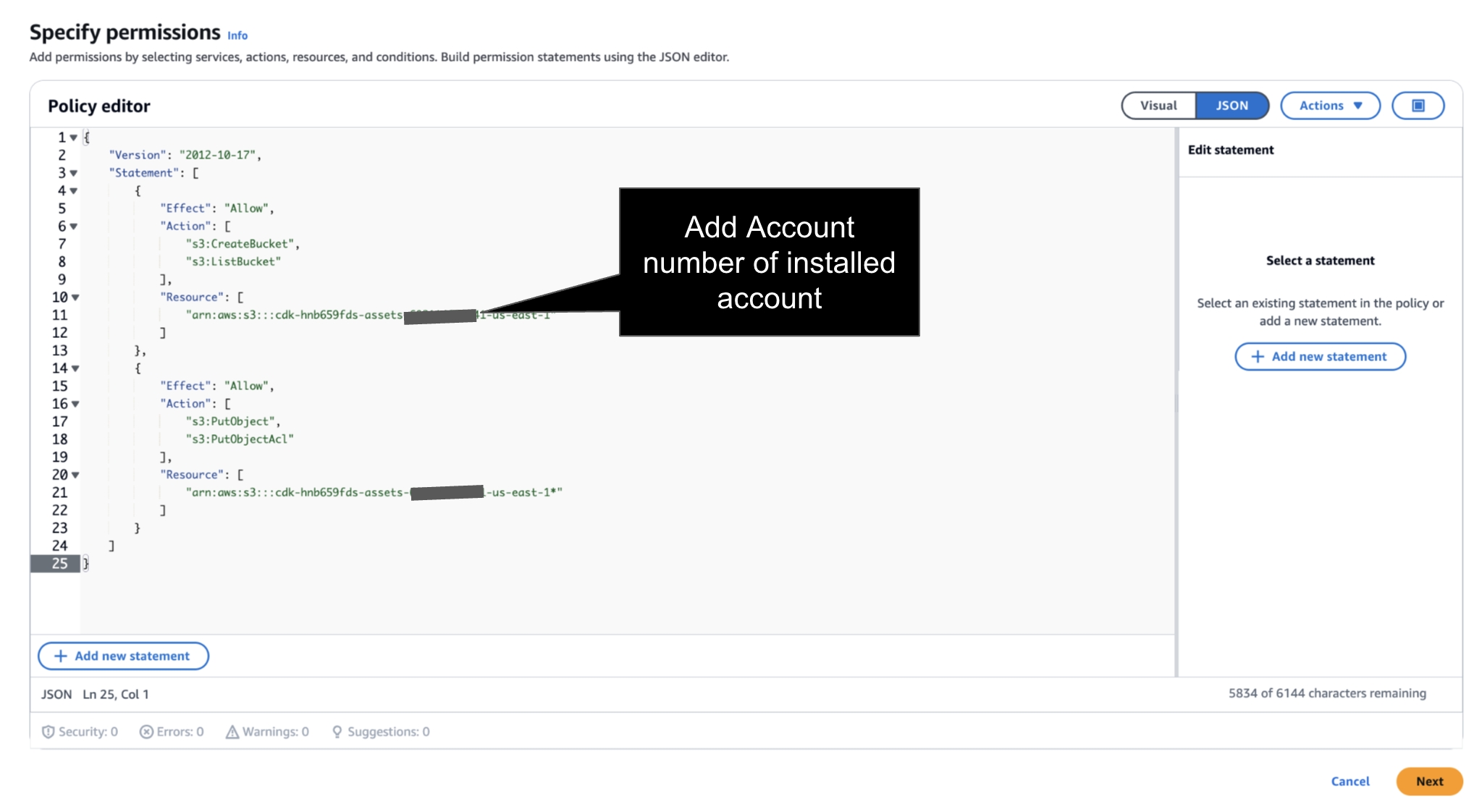
Prior to Launch → the IAM Instance Profile much have a Role with Policy to S3 Create Bucket and S3 Write Access for FinOps Center Installation Bucket. Add your AWS Account Number to below Policies.
Navigate to IAM and follow below Steps
Step 1: Create a New Role for EC2 or Validate an Existing Role has above Policy.
Click to Zoom
JSON Policy - add account number of installed account.
Step 2: Create a Role
Click to Zoom
Step 3: Add Policy to Role
Click to Zoom
and Create Role
Click to Zoom
Return to EC2 to Launch Instance
No Key is Required as the Instance can be delete upon Install
Launch Instance
Navigate to S3
As the EC2 starts up, a bucket will appear beginning with cdk (see below)
Once you see the cdk Bucket is created navigate back to the Marketplace Listing to Launch CloudFormation.
Launch CloudFormation
Click Next
Note: All environment installation are “ Fresh Installs”. There is no separate installation pipeline between SDLC environment.
FinOps Center
FinOps Center is a web application that may experience typical issues from users around login issues or page loading (especially updates). Additionally, during the initial 24hrs of installing FinOps Center the application may be awaiting data population from the Cost & Usage Report (CUR).
If users are having issues with their initial logging into FinOps Center it could be an issue with the Cognito temporary password. It is common that the remedy is to delete the users from the Cognito User Pool and Re-Create them in the FinOps Center Configuration.
During initial configuration of the application the AWS CUR Data is not loading you may need to wait until the next cycle to run. Have a member of your technical team navigate to the S3 bucket in the FinOps Center installed account and view when the last CUR was created keeping in mind that the CUR creation time is UCT. If a CUR cycle has run after the time of the upload of the Chart/Budget File, contact support.
Agent Bill Amazon Q in QuickSight
If users are having issues accessing the Amazon Q in QuickSight Topics, validate that the following are configured apppriately:
The FinOps Center application URL has been added to the QuickSight Admin
Validate in the Topic ID has been added to the Configuration Page
Validate that the Topics have been added to the Role from the QuickSight Console
if you can't see the Topics, validate that your Author Pro has the Topics Role
Agent Bill Agentic CFM
Cost Optimization Hub Data
If Cost Optimization Hub Data is not loading in the Cost Optiizatoin Raw Table,, navigate to the Lambda service in the Console (CostOptimizationLambda881C3E41) and run Test to trigger the Lambda.
Agentcore ECS tasks stuck in provisioning
VPC endpoint missing or SG restricts outbound
Validate required Interface Endpoints (S3, DynamoDB, STS, Secrets Manager, AppSync, Bedrock) exist and SG outbound is not 0.0.0.0/0 denied
Client application cannot reach AgentCore MCP endpoint
Wrong ALB DNS used or not using HTTPS 443
Validate the endpoint using curl -v https://<agentcore-alb-dns>/health — must return 200
AgentCore cannot invoke FinOps Center API
IAM trust misalignment between delegated admin and linked accounts
Validate delegated admin role trust using STS AssumeRole test from AgentCore ECS task execution role
AppSync returns unauthorized
missing JWT validator / wrong signature key
Validate JWT issuer matches AgentCore Identity config. re-rotate token + test via AppSync Console with same token
Lambda invoked but no FinOps process executes
missing FinOps Center permission boundary or missing PK Tenant prefix

Validate Dynamo Partition Key prefix matches defined TenantID for that deployment
cdk-xxxxxx-assets-accountnumber-us-east-1
US East (N. Virginia) us-east-1
Bucket and objects not public
Timestamp
FinOps Center leverages native services encryption of data at rest and in transit.
All FinOps Center data is stored in S3 or DynamoDB when at rest. When users are accessing the application CloudFront provides the SSL connection for the frontend application.
Data at Rest:
S3 Server-Side Encryption (SSE):
SSE-S3: Encrypts objects using AES-256, managed by S3.
SSE-KMS: Uses AWS Key Management Service (KMS) for encryption keys, giving more control over key policies and auditability.
SSE-C: Customer-provided encryption keys, if you prefer to manage keys outside AWS.
Client-Side Encryption: Use AWS SDK for encryption before uploading objects to S3. You manage keys and encrypt data client-side.
Data in Transit:
Use HTTPS (TLS 1.2 or higher) for all communications to and from S3.
Enforce HTTPS using S3 bucket policies or CloudFront distribution.
Data at Rest:
QuickSight encrypts your data at rest using AWS KMS by default.
For additional control, configure your own KMS Customer Managed Key (CMK) for QuickSight to use.
Data in Transit:
All communication between QuickSight, S3, and other AWS services is protected using TLS 1.2.
Embedded Dashboards:
Use secure HTTPS connections for embedding dashboards within your React frontend.
FinOps Center Custom IAM policies and Row-Level Security (RLS) to ensure users only see authorized data.
Data at Rest:
By default, AWS Lambda encrypts deployment packages and environment variables at rest using AWS-managed keys.
For additional control, use KMS for:
Encrypting environment variables (configure KMS keys in Lambda function settings).
Encrypting sensitive application secrets (e.g., credentials, tokens) stored in AWS Secrets Manager or SSM Parameter Store.
Data in Transit:
All data passed to and from Lambda is encrypted using TLS 1.2.
Use HTTPS endpoints for API Gateway and other services invoked by Lambda.
Data at Rest:
Default Encryption with AWS KMS: All DynamoDB tables are encrypted at rest using AES-256.
Use Customer Managed KMS Keys (CMK) for:
More control over the encryption keys.
Auditability and fine-grained key management.
Data in Transit:
All DynamoDB connections use TLS 1.2 to secure data in transit.
Enforce the use of HTTPS for all interactions with DynamoDB.
Use AWS Key Management Service (KMS) to unify encryption management across services like S3, Lambda, DynamoDB, and QuickSight.
Monitor key usage with AWS CloudTrail for auditing encryption activities.
AWS CloudTrail: Track key usage, access logs, and API calls.
AWS CloudWatch: Monitor encryption-related metrics.
AWS Config: Ensure encryption configurations remain compliant with best practices.
Agent Bill Bedrock Agent
Agent Bill has an additional encrypted connection between the MCP Server on Lambda to the Bedrock Agent/Action Group.
Data in Transit:
All data passed to and from Lambda (MCP Server) is encrypted using TLS 1.2.
Use HTTPS endpoints for API Gateway and other services invoked by Lambda.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:CreateBucket",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::cdk-hnb659fds-assets-<accountnumber>-us-east-1"
]
},
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::cdk-hnb659fds-assets-<accountnumber>-us-east-1*"
]
}
]
} DynamoDB (Data Storage)
AWS KMS (default or CMK)
TLS 1.2 (HTTPS)
Enforce HTTPS for DynamoDB connections.
Component
At Rest
In Transit
Additional Notes
S3 (React Frontend)
SSE-S3, SSE-KMS, SSE-C, Client-Side
TLS 1.2 (HTTPS)
Enforce HTTPS using policies.
QuickSight
AWS KMS (default or CMK)
TLS 1.2
Use IAM and Row-Level Security (RLS).
Lambda (Business Logic)
AWS KMS for environment variables
TLS 1.2
Use KMS for Secrets Manager or SSM data.
Upon completion of the FinOps Center installation, log into the AWS Account of the applicatoin and navigate to the Amazon Cognito Service and the FinOpsCenterPool
In the left hand navigation, click on the Manage Template and sellect Invitation Message then Edit.
Add Welcome to FinOps Center in the Subject
The Recommended HTML that requires an update for your FinOps Center URL
Note: href needs to be changed to application url




<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Welcome to FinOps Center</title>
<style type="text/css">
/* Import Lato font */
@import url('https://fonts.googleapis.com/css2?family=Lato:wght@400;700&display=swap');
/* Reset styles for email clients */
body, table, td, p, a, li, blockquote {
-webkit-text-size-adjust: 100%;
-ms-text-size-adjust: 100%;
}
body {
margin: 0;
padding: 0;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
line-height: 1.6;
color: #333333;
background-color: #f0f4f8;
}
table {
border-spacing: 0;
border-collapse: collapse;
mso-table-lspace: 0pt;
mso-table-rspace: 0pt;
}
img {
border: 0;
height: auto;
line-height: 100%;
outline: none;
text-decoration: none;
-ms-interpolation-mode: bicubic;
}
/* Main container */
.container {
max-width: 600px;
margin: 0 auto;
background-color: #ffffff;
border-radius: 8px;
overflow: hidden;
box-shadow: 0 3px 10px rgba(0, 0, 0, 0.1);
}
/* Header */
.header {
padding: 30px 0;
text-align: center;
background-color: #000000;
color: #ffffff;
}
/* Logo */
.header img {
border: 0;
display: block;
margin: 0 auto;
max-width: 80%;
height: auto;
}
/* Content */
.content {
padding: 30px;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
}
/* Credentials box */
.credentials-box {
background-color: #e0f7fa;
border: 1px solid #b2ebf2;
border-radius: 5px;
padding: 20px;
margin: 20px 0;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
}
.credentials-item {
margin-bottom: 10px;
}
.credentials-label {
font-weight: bold;
display: inline-block;
width: 120px;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
color: #00363a;
}
.credentials-value {
font-family: monospace;
background-color: #ffffff;
padding: 3px 6px;
border-radius: 3px;
border: 1px solid #b2ebf2;
color: #006064;
}
/* Button */
.button-container {
text-align: center;
margin: 30px 0;
}
.button {
display: inline-block;
background-color: #ffc107;
color: #333333 !important;
text-decoration: none;
padding: 12px 30px;
border-radius: 4px;
font-weight: bold;
font-size: 16px;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
box-shadow: 0 2px 5px rgba(0, 0, 0, 0.1);
}
/* Footer */
.footer {
padding: 20px;
text-align: center;
font-size: 12px;
color: #666666;
background-color: #e0f7fa;
font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;
border-top: 1px solid #b2ebf2;
}
a {
color: #00838f;
text-decoration: underline;
}
/* Responsive adjustments */
@media screen and (max-width: 600px) {
.container {
width: 100% !important;
border-radius: 0;
}
.content {
padding: 20px !important;
}
.credentials-label {
display: block;
width: 100%;
margin-bottom: 5px;
}
}
</style>
</head>
<body>
<table width="100%" border="0" cellpadding="0" cellspacing="0" bgcolor="#f0f4f8">
<tr>
<td align="center" style="padding: 40px 0;">
<table class="container" width="600" border="0" cellpadding="0" cellspacing="0">
<!-- Header -->
<tr>
<td class="header">
<img src="https://finopscenterlogobin.s3.amazonaws.com/FinOpsCenter_VerticalLogo_Main.png" alt="FinOps Center Logo" width="250" style="max-width: 80%; height: auto; display: block; margin: 0 auto;">
</td>
</tr>
<!-- Content -->
<tr>
<td class="content">
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #333333;">Hello,</p>
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #333333;">Your FinOps Center account has been created successfully. Below are your login credentials:</p>
<!-- Credentials Box -->
<div class="credentials-box">
<div class="credentials-item">
<span class="credentials-label">Username:</span>
<span class="credentials-value">{username}</span>
</div>
<div class="credentials-item">
<span class="credentials-label">Temporary Password:</span>
<span class="credentials-value">{####}</span>
</div>
</div>
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #333333;">For security reasons, you will be required to change your password upon your first login.</p>
<!-- Button -->
<div class="button-container">
<a href="https://<<FinOps Center/login" class="button" style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif;">Access FinOps Center</a>
</div>
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #333333;">If you have any questions or need assistance, please visit <a href="https://www.finopscenter.com/support" style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #00838f;">www.finopscenter.com/support</a>.</p>
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #333333;">Thank you,<br>The FinOps Center Team</p>
</td>
</tr>
<!-- Footer -->
<tr>
<td class="footer">
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #666666;">© 2025 Cloud Scal3 Inc. All rights reserved.</p>
<p style="font-family: 'Lato', 'Helvetica Neue', Helvetica, Arial, sans-serif; color: #666666;">This is an automated email. Please do not reply to this message.</p>
</td>
</tr>
</table>
</td>
</tr>
</table>
</body>
</html>

Logical
Services
accountbudgetlambdarole77006F98
AWS::IAM::Role
accountbudgetlambdaroleDefaultPolicy4FB21BEA
AWS::IAM::Policy
AccountBudgetTable0C66D07B
AWS::DynamoDB::Table
AccountMapping4D0F5AFB
AWS::DynamoDB::Table
During the installation of FinOps Center, the following roles are created in customers accounts:
Lambda access to write data dynamodb table (InvoiceTable)
quicksightaccessrole80E5A653
Lambda to get quicksight dashboard url programatically
FinOpsCenterFinopsInaBoxBudgetAllocationApilambdaDatasourceServiceRoleE3C454C3
Appsync to invoke lambda function named BudgetAllocationLambda
FinOpsCenterFinopsInaBoxBudgetAllocationApibudgetApprovalLambdaDatasourceServiceRole59BD64A6
Appsync to invoke lambda function named BudgetApprovalLambda
FinOpsCenterFinopsInaBoxBudgetAllocationApiquickSightLambdaDatasourceServiceRoleDC35C747
Appsync to invoke lambda function named QuicksightLambda
FinOpsCenterFinopsInaBoxBudgetAllocationApischedulerLambdaDatasourceServiceRole5D04EA71
Appsync to invoke lambda function named SchedulerLambda
FinOpsCenterFinopsInaBoxBudgetAllocationApiinvoiceLambdaDatasourceServiceRoleD85B21E4
appsync to invoke lambda function named InvoiceLambda
FinOpsCenterFinopsInaBoxBudgetAllocationApiauthenticationLambdaDatasourceServiceRole0DAF3D85
appsync to invoke lambda function named AuthenticationLambda
accountbudgetlambdarole77006F98
lambda access to write data dynamodb table (SorElementToKeyMapper, BudgetsFromSOR)
FinOpsCenterFinopsInaBoxSchedulerLambdaHandlerServiceRole1D4A6F1E
lambda access to write data dynamodb table (Scheduler)
FinOpsCenterFinopsInaBoxAuthenticationLambdaHandlerServiceRole3583A726
lambda access to Cognito
CustomCDKBucketDeployment8693BB64968944B69AAFB0CC9EB8756CServiceRole89A01265
Lambda access to S3
athenaexecutionroleDefaultPolicy7907B333
Athena access for CUR Data Import
S3NotificationResourceCustomResourcePolicy0EC084AF
Bucket to trigger lambda on new items upload
executionroleDefaultPolicy497F11A3
BucketNotificationsHandler050a0587b7544547bf325f094a3db834RoleDefaultPolicy2CF63D36
Bucket to trigger lambda on new items upload
budgetApprovalLambdaHandlerServiceRoleDefaultPolicyDE143198
budgetTriggerLambdaHandlerServiceRoleDefaultPolicyDD9AEFCA
Bucket to trigger lambda on new items upload
BudgetApprovalStateMachineRoleDefaultPolicyF89BE0F0,
Step Function Execution
invoiceLambdaHandlerServiceRoleDefaultPolicy20D94148
Bucket to trigger lambda on new items upload
quicksightaccessroleDefaultPolicy15628D24
Access to QuickSight Assets
FinOpsCenterFinopsInaBoxBudgetAllocationApilambdaDatasourceServiceRoleDefaultPolicyECB450A3
Access to DynamoDB for Step Function
FinOpsCenterFinopsInaBoxBudgetAllocationApibudgetApprovalLambdaDatasourceServiceRoleDefaultPolicyBCD48E00
Step Function Execution
FinOpsCenterFinopsInaBoxBudgetAllocationApiquickSightLambdaDatasourceServiceRoleDefaultPolicyE116784C
Access to QuickSight Assets for Row Level Security
FinOpsCenterFinopsInaBoxBudgetAllocationApiquickSightLambdaDatasourceServiceRoleDefaultPolicyE116784C
Access to QuickSight Assets for Row Level Security
FinOpsCenterFinopsInaBoxBudgetAllocationApiquickSightLambdaDatasourceServiceRoleDefaultPolicyE116784C
Access to QuickSight Assets for Row Level Security
FinOpsCenterFinopsInaBoxBudgetAllocationApischedulerLambdaDatasourceServiceRoleDefaultPolicyC73BC128
Access to DynamoDB for Step Function
FinOpsCenterFinopsInaBoxBudgetAllocationApiinvoiceLambdaDatasourceServiceRoleDefaultPolicyF3F771EC
Access to DynamoDB for Step Function
FinOpsCenterFinopsInaBoxBudgetAllocationApiauthenticationLambdaDatasourceServiceRoleDefaultPolicyEDD13462
Access to Cognito for Authenticationo
accountbudgetlambdaroleDefaultPolicy4FB21BEA
Step Function Execution
FinOpsCenterFinopsInaBoxSchedulerLambdaHandlerServiceRoleDefaultPolicy0A59ABD5
Step Function Execution
FinOpsCenterFinopsInaBoxAuthenticationLambdaHandlerServiceRoleDefaultPolicy28CCCF9A
Access to Cognito for Authentication
CustomCDKBucketDeployment8693BB64968944B69AAFB0CC9EB8756CServiceRoleDefaultPolicy88902FDF
Execution to Create S3 bucket for FinOps Center Deployment
QSManagedPolicyBC3B1016
AccountToElement1Mapping752D6570
AWS::DynamoDB::Table
AccountMapping4D0F5AFB
AWS::DynamoDB::Table
AccountToElement1Mapping752D6570
AWS::DynamoDB::Table
AccountToElement2MappingC5E21C49
AWS::DynamoDB::Table
AccountToElement3MappingA58D0E58
AWS::DynamoDB::Table
AccountToElement4Mapping7A6110D3
AWS::DynamoDB::Table
Admins
AWS::Cognito::UserPoolGroup
adminUser
AWS::Cognito::UserPoolUser
ApprovedBudgetsTableA2AC60E6
AWS::DynamoDB::Table
athenaexecutionrole33E3CAB2
AWS::IAM::Role
athenaexecutionroleDefaultPolicy7907B333
AWS::IAM::Policy
AthenaPolicyCADD8C34
AWS::IAM::ManagedPolicy
athenatemp87F857C8
AWS::S3::Bucket
AWS679f53fac002430cb0da5b7982bd22872D164C4C
AWS::Lambda::Function
AWS679f53fac002430cb0da5b7982bd2287ServiceRoleC1EA0FF2
AWS::IAM::Role
BucketNotificationsHandler050a0587b7544547bf325f094a3db8347ECC3691
AWS::Lambda::Function
BucketNotificationsHandler050a0587b7544547bf325f094a3db834RoleB6FB88EC
AWS::IAM::Role
BucketNotificationsHandler050a0587b7544547bf325f094a3db834RoleDefaultPolicy2CF63D36
AWS::IAM::Policy
budgetApprovalLambdaHandlerD5A8C414
AWS::Lambda::Function
budgetApprovalLambdaHandlerServiceRole57D52BE3
AWS::IAM::Role
budgetApprovalLambdaHandlerServiceRoleDefaultPolicyDE143198
AWS::IAM::Policy
BudgetApprovalStateMachine749086CB
AWS::StepFunctions::StateMachine
BudgetApprovalStateMachineRole7D20BD03
AWS::IAM::Role
BudgetApprovalStateMachineRoleDefaultPolicyF89BE0F0
AWS::IAM::Policy
BudgetApprovalWorkflow471D8ADC
AWS::DynamoDB::Table
BudgetsFromSOR1281753B
AWS::DynamoDB::Table
budgetTriggerLambdaHandler47313A97
AWS::Lambda::Function
budgetTriggerLambdaHandlerServiceRoleB543531A
AWS::IAM::Role
budgetTriggerLambdaHandlerServiceRoleDefaultPolicyDD9AEFCA
AWS::IAM::Policy
BUManagers
AWS::Cognito::UserPoolGroup
CDKMetadata
AWS::CDK::Metadata
curExtractorLambdaHandler527EA93F
AWS::Lambda::Function
curExtractorLambdaHandlerAllowS3InvocationDD55202D
AWS::Lambda::Permission
CustomCDKBucketDeployment8693BB64968944B69AAFB0CC9EB8756C81C01536
AWS::Lambda::Function
CustomCDKBucketDeployment8693BB64968944B69AAFB0CC9EB8756CServiceRole89A01265
AWS::IAM::Role
CustomCDKBucketDeployment8693BB64968944B69AAFB0CC9EB8756CServiceRoleDefaultPolicy88902FDF
AWS::IAM::Policy
DepartmentManagers
AWS::Cognito::UserPoolGroup
Element1Mapping4380F9B0
AWS::DynamoDB::Table
Element2MappingE36F9FE4
AWS::DynamoDB::Table
Element3Mapping4C6A994A
AWS::DynamoDB::Table
Element4Mapping2FFF5F38
AWS::DynamoDB::Table
executionroleD9A39BE6
AWS::IAM::Role
executionroleDefaultPolicy497F11A3
AWS::IAM::Policy
FinancialAdmins
AWS::Cognito::UserPoolGroup
FinOpsCenterAccountBudgetLambdaHandler8229024E
AWS::Lambda::Function
FinOpsCenterAuthenticationLambdaHandler7B901A70
AWS::Lambda::Function
FinOpsCenterAuthenticationLambdaHandlerServiceRoleDefaultPolicy9C018194
AWS::IAM::Policy
FinOpsCenterAuthenticationLambdaHandlerServiceRoleF2924748
AWS::IAM::Role
FinOpsCenterBudgetAllocationApi830C7F83
AWS::AppSync::GraphQLApi
FinOpsCenterBudgetAllocationApiauthenticationLambdaDatasource22C76159
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApiauthenticationLambdaDatasourceServiceRole8F2BC046
AWS::IAM::Role
FinOpsCenterBudgetAllocationApiauthenticationLambdaDatasourceServiceRoleDefaultPolicyABAF4045
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApibudgetApprovalLambdaDatasourceA40E713B
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApibudgetApprovalLambdaDatasourceServiceRole5098C713
AWS::IAM::Role
FinOpsCenterBudgetAllocationApibudgetApprovalLambdaDatasourceServiceRoleDefaultPolicy9EC99F1C
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApicanCloseMonthResolver2E01B50A
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApichangePasswordResolver3C958E69
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicompletePasswordChallengeResolver30910FB5
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiconfirmPasswordResolverFDF56F2F
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateAccountMappingResolver7B079C58
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateAllocationResolver225FB95A
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateBudgetResolver64D61C0E
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateInvoiceResolver43BD5274
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateOrUpdateDashboardResolverA81AB980
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateOrUpdateSpaceDetailsResolver537D1657
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateOrUpdateUserToBudgetAccessResolverE080EDB5
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateUserMappingResolver7D63193A
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApicreateUserResolverA1E605E3
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApidefaultApiKey300A2538
AWS::AppSync::ApiKey
FinOpsCenterBudgetAllocationApideleteAllocationResolver4650763F
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiforgotPasswordResolver42502E8F
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetAllBudgetsNewResolverC85C0932
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetAllBudgetsResolverB935009A
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetDashboardListResolver72B95653
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetInvoicesResolverC4F37F86
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetLastRunCurResolver24E9B10E
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetPeriodCardsForUserResolver2086F8FC
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetQuickSightDashboardUrlResolverE9D8DE12
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetSorListByYearResolverCD447711
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetSorMappingResolverDD843F7B
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetTimeCardsForUserResolver4FC1F4CD
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUnallocatedAccountsResolver3432E36F
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUsageActualsForUserResolverDBEAA204
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUsageDetailsForUserNewResolver746CB582
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUsageDetailsForUserResolver6EF10137
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUsageStatsResolverAED9AFEA
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApigetUserMappingToBudgetsAndAccountsResolverAA475845
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiinvoiceLambdaDatasource999FAA93
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApiinvoiceLambdaDatasourceServiceRole833AADEB
AWS::IAM::Role
FinOpsCenterBudgetAllocationApiinvoiceLambdaDatasourceServiceRoleDefaultPolicyAD0CDF57
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApilambdaDatasourceAB665C33
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApilambdaDatasourceServiceRole7144E454
AWS::IAM::Role
FinOpsCenterBudgetAllocationApilambdaDatasourceServiceRoleDefaultPolicy440E4797
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApilistAccountMappingResolver34043668
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistAccountsResolver56E8C48D
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistAllocationsResolver6165ADBD
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistGroupsResolverDCFF3E28
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistSpacesResolver60ED72B7
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistUserBudgetAllocationsResolver78C6B1CF
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistUserMappingResolverC3FFF016
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApilistUsersResolver8B930FB7
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiloginUserResolver48621D0D
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApimonthCloseResolver17AA178F
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiquickSightLambdaDatasource42753279
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApiquickSightLambdaDatasourceServiceRole9A3B29C1
AWS::IAM::Role
FinOpsCenterBudgetAllocationApiquickSightLambdaDatasourceServiceRoleDefaultPolicy21D8C2A6
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApireviewBudgetResolverB4A7AD9A
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApischedulerLambdaDatasourceDF97F9B9
AWS::AppSync::DataSource
FinOpsCenterBudgetAllocationApischedulerLambdaDatasourceServiceRole0E24BE0C
AWS::IAM::Role
FinOpsCenterBudgetAllocationApischedulerLambdaDatasourceServiceRoleDefaultPolicy8D806BF5
AWS::IAM::Policy
FinOpsCenterBudgetAllocationApiSchema6D45E612
AWS::AppSync::GraphQLSchema
FinOpsCenterBudgetAllocationApisorMappingResolver822F3A5B
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiupdateAccountsWithOrganizationsInfoResolver91CC1D41
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiupdateAllocationResolver8A725FFD
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiupdateBudgetResolver2EDA782E
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiupdateTimeCardStatusResolver66B4C127
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiupdateUserRoleResolverBE9C313C
AWS::AppSync::Resolver
FinOpsCenterBudgetAllocationApiuploadSORResolver08F81E2F
AWS::AppSync::Resolver
FinOpsCenterQuickSightLambdaHandler796799F3
AWS::Lambda::Function
FinOpsCenterSchedulerLambdaHandler044C0558
AWS::Lambda::Function
FinOpsCenterSchedulerLambdaHandlerServiceRole44BD75A8
AWS::IAM::Role
FinOpsCenterSchedulerLambdaHandlerServiceRoleDefaultPolicyA6553EC0
AWS::IAM::Policy
FinOpsCenterScheduleRuleAllowEventRuleFinOpsCenterStackFinOpsCenterSchedulerLambdaHandler680625AE3E90D379
AWS::Lambda::Permission
FinOpsCenterScheduleRuleEDEF0E06
AWS::Events::Rule
FinOpsCenterSharedFunctionsLayer84909F55
AWS::Lambda::LayerVersion
GluePolicyCA7268D5
AWS::IAM::ManagedPolicy
invoiceLambdaHandler083AEC55
AWS::Lambda::Function
invoiceLambdaHandlerServiceRoleAD7C6EE6
AWS::IAM::Role
invoiceLambdaHandlerServiceRoleDefaultPolicy20D94148
AWS::IAM::Policy
InvoiceTableD753B0E0
AWS::DynamoDB::Table
LastUpdatedTableD54B2C25
AWS::DynamoDB::Table
PortfolioManagers
AWS::Cognito::UserPoolGroup
ProductManagers
AWS::Cognito::UserPoolGroup
QSManagedPolicyBC3B1016
AWS::IAM::ManagedPolicy
quicksightaccessrole80E5A653
AWS::IAM::Role
quicksightaccessroleDefaultPolicy15628D24
AWS::IAM::Policy
QuicksightTable0E76B5B0
AWS::DynamoDB::Table
S3NotificationResourceCustomResourcePolicy0EC084AF
AWS::IAM::Policy
S3NotificationResourceF98D77E7
Custom::AWS
S3Policy8FACFAB8
AWS::IAM::ManagedPolicy
SorElementToKeyMapper64C55F7A
AWS::DynamoDB::Table
SORExtractorLambda56652A5B
AWS::Lambda::Function
sorfiles6743E409
AWS::S3::Bucket
sorfilesAllowBucketNotificationsToFinOpsCenterStackSORExtractorLambdaA4B317F72869BA7F
AWS::Lambda::Permission
sorfilesNotifications4210B679
Custom::S3BucketNotifications
SpacesTable8A997355
AWS::DynamoDB::Table
staticContentDeploymentAwsCliLayer18F25694
AWS::Lambda::LayerVersion
staticContentDeploymentCustomResourceC4584F3F
Custom::CDKBucketDeployment
TimeCardsTable0247B46C
AWS::DynamoDB::Table
UsageAccountsTable883695CF
AWS::DynamoDB::Table
UsageAccountToServiceDailyTable3EF26074
AWS::DynamoDB::Table
UsageAccountToServiceTableD3843CFA
AWS::DynamoDB::Table
UsageDailyTable837F89FC
AWS::DynamoDB::Table
UsageMasterAccountsTableD91A7B5C
AWS::DynamoDB::Table
UsageTable28300137
AWS::DynamoDB::Table
UserBudgetAccessTable665F2C92
AWS::DynamoDB::Table
UserMappingABB16FE5
AWS::DynamoDB::Table
UserPool6BA7E5F2
AWS::Cognito::UserPool
UserPoolFinOpsCenterPoolweb6108E3D9
AWS::Cognito::UserPoolClient
Resource/Role
Purpose
athenaexecutionrole33E3CAB2
Lambda Execute Role for Athena queries
AWS679f53fac002430cb0da5b7982bd2287ServiceRoleC1EA0FF2, executionroleD9A39BE6
Lambda to Read files from s3 bucket
BucketNotificationsHandler050a0587b7544547bf325f094a3db834RoleB6FB88EC
S3Bucket trigger for lambda on new file upload
budgetApprovalLambdaHandlerServiceRole57D52BE3
Lambda to write data to DynamoDB tables (BudgetApprovalWorkflow, ApprovedBudgetsTable)
budgetTriggerLambdaHandlerServiceRoleB543531A
Lambda to Write data to dynamodb table (BudgetApprovalWorkflow, ApprovedBudgetsTable)
BudgetApprovalStateMachineRole7D20BD03,
Lambda access to trigger step function
invoiceLambdaHandlerServiceRoleAD7C6EE6